Why Physical Access Wins
I have just had a job explaining to friend that allowing Physical Access to a PC can reveal quite alot. Even if the PC is off. His problem was understanding that not only can an attacker Access all of the information on that PC he can also extract the passwords of anyone who has logged onto it in the past.
So in the scenario where an administrator has logged onto a laptop in the workplace, then the employee takes the laptop home and an unauthorized person has Access to the laptop it is relatively easy to reset the local admin password to provide the attacker with admin Access to the laptop and from there he can load up some free software and pull off the cached credentials of anyone who has accessed the laptop, such as the administrator from the office.
Obviously it's not just attackers who could do this, a rogue employee could quite easily create a situation where someone with higher levels of Access must log onto their PC and then take that laptop home and extract the password that was used.
Tools
So if the attacker was the employee, he can see who and when another user has logged on to their PC by looking at the ********s and Settings folder and seeing what profiles are created.
Next (this is assuming a standard employee doesn't have admin rights to the PC), after creating a boot disk for a utility such as NTpasswd the PC can be booted with it and the local administrator password can be changed.

After booting up and logging in as the local administrator, the attacker could load a tool such as Cain & Abel and extract the hashes of the cached credentials from that PC.

And then crack them using a number of different methods.

It really is that simple.
Another great tool (although not free) for extracting cached credentials is Elcomsoft's Proactive System Password Recovery tool.
Below is a screenshot of that tool in action on the same PC.

Prevention
Well it's really hard to prevent a rogue employee from doing things like this but things like not giving Domain Admin rights to IT support personnel, and only have an account with domain admin rights to perform domain admin tasks will help. Extra strong password on those accounts is also a really good option. For unauthorized people accessing those laptops, BIOS and boot passwords will make the job harder for them and of course full disk encryption would help loads.
Thats it for this short post.
Links
http://home.eunet.no/pnordahl/ntpasswd/
http://www.oxid.it/
http://www.elcomsoft.com/pspr.html
Thursday, May 1, 2008
Okay there are plenty of tools to launch password attacks within Windows but I like this one because it needs no tools other than those that are native to Windows.
The only difficult bit is getting the wordlist together. If anyone knows of a funky way to generate one using native windows tools and existing files on a PC I would love to hear from you. In lieu of a funky solution and without a wordlist that I have got to the box by other means I make my list by creating a file with popular passwords and hope for the best. Remember, if you are making the wordlist, tune it for the company or organisation you are pentesting against.
This attack is going to bruteforce a password using a FOR loop and a text file with some passwords in.
How it Works
Make sure you have a wordlist or create one with possible password in. The password file just needs to be a normal test file with a word on each line.

At the command prompt on one line type:
FOR /F "tokens=1*" %i in (passwords.txt) do net use \\192.168.1.1\IPC$ %i /u:Administrator
The password.txt file must be in the same directory that you run the command from.
Whats happening here is the command attempting to connect to the IPC$ share on 192.168.1.1 and is going through the file password.txt trying every word as a password for the Administrator account.
You don't have to specify the IPC$ share. If there is another share available you can use that.
Obviously this attack can be done on other accounts but remember that they may be subject to lockout after so many failed logins. The Administrator account does not get locked out.
If you find that the account lock out policy is not enforced then you can create a password file with usernames and password in (separated by a space), then throw the file at it using a FOR loop shown in my screenshot.

If you have found a successful pair the outcome will be a open session (net use) and the file out.txt will list the valid credentials.
Lessons learned for Admins
- Pick a good Administrator password that will not be in a dictionary. and enforce complex passwords for users.
- Make sure that account lock out policies are enforced.
- Educate users and helpdesk staff. If they notice that accounts are constantly locked out and the user is not too stupid then they might be your early warning system that something is wrong.
- Check logs. Account lockouts should be logged and you should be seeing this type of activity in you daily log monitoring routine.
Label
Saturday, February 9, 2008
The purpose of this post is to demonstrate how an attacker may use free tools to bruteforce passwords and gain Access to sensitive information.
The tools I use in this example are from BackTrack3.
Tools
- Backtrack
- NMap
- HydraGTK (using John's wordlist)
- Medusa
- snmpcheck.pl
The Attack
1. If I don't already have a list of targets and services I would use nmap to scan for services and systems that I know I can perform an attack against.
nmap 192.168.2.2 -T 4 -sV -P0 -n

Remember, In an attack scenario it is can be a good idea to scan only those services that you have working exploits for or that you know your tools can run password lists against.
2. Following a rather unstealthy scan I see that my target has a FTP Server and some NETBIOS ports open (139 & 445). These service are perfect for my tools, I know that I can peform a bruteforce attack on either one.
Listed below are all the protocols and services that Hydra can perform attacks against:
TELNET, FTP, HTTP-GET, HTTP-HEAD, HTTPS-GET, HTTP-HEAD, HTTP-PROXY,
HTTP-PROXY-NTLM, HTTP-FORM-GET HTTP-FORM-POST, HTTPS-FORM-GET,
HTTPS-FORM-POSTLDAP2, LADP3, SMB, SMBNT, MS-SQL, MYSQL, POSTGRES,
POP3-NTLM, IMAP, IMAP-NTLM, NNTP, PCNFS, ICQ, SAP/R3, Cisco auth,
Cisco enable, SMTP-AUTH, SMTP-AUTH-NTLM, SSH2, SNMP, CVS, Cisco AAA,
REXEC, SOCKS5, VNC, POP3 and VMware-Auth
Either using hydra (commandline) or HydraGTK (GUI) I enter a known or likely username or specify a list of valid or likely usernames if I have them (there is more on this in the following SNMP section).

3. Now I enter the IP or name of your target and I select a service that was available on the target when I performed my nmap scan. I have chosen ftp for this example.

4. Now I give hydra a wordlist. I have just given it johns wordlist here (on BackTrack3 in /usr/local/john-1.7.2/password.lst) For better results I would usually give hydra a bigger list. I have also chosen to try null passwords and try the username as the password.

5. The next tab gives me options for tuning Hydra. I can tell Hydra to stop checking after is has found a match, this may restrict the number of valid usernames and passwords found but it will be quieter. Proxy settings can also be set here.

6. Specific options can be set on the next tab.

7. Now I have all my settings configured I kick it off and await the joy.

Any results can be save to a file.
If I had wanted to perform the same attack from the commandline I would have used the following syntax:
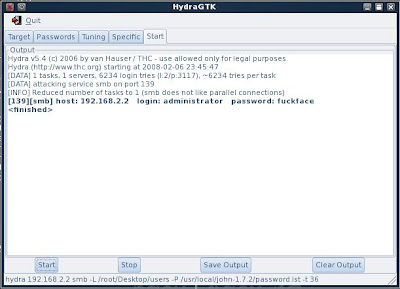
hydra 192.168.2.2 -l administrator -P /usr/local/john-1.7.2/password.lst -t 36

Obviously this is slightly quicker but the GUI is fun and useful to become familiar with Hydra.
Below is another successful attack on the smb protocol (port 139)
SNMP
Supposing I don't have any username but I find that port 161 UDP is open? Well that usually means that SNMP is up. Hydra can then be used to bruteforce the SNMP community strings and if successful I can get to the entire config on the server including a complete list of users. Here's how.
The Attack
1. I configure hydra with no username and as a password i use "public" which is the default. If that fails I give hydra a password list to try.

2. Following a successful guess I use the SNMP string with another tool from BackTrack called snmpcheck.pl
./snmpcheck-1.6.pl -t 192.168.2.2 -c secret -l -v 2

This tool will now pull down all the info on my target and i can extract the user names into a file to feed back into Hydra as valid usernames

How To Protect Yourself
Having an account lockout policy is one protection available, but I often wonder if after several attacks someone would get pissed off with locked out accounts and remove the policy.
Also, SNMP should not use the default community strings and can be locked down so only certain devices talk to each other. SNMP traffic can also be encrypted.
Another weakness this tool exploits is weak passwords. If users have strong passwords they may still be cracked however, the attacker may need to get a little noisier and you may just see him in the logs. You are checking the logs aren't you?
Oh, and one last thing on passwords. Remember to change the default passwords on all devices.
Note: I will update this post with other useful tools as i find time.
Satur
Creating Custom Password Lists
This blog entry is on how to quickly create a custom wordlist to use with a password cracker. This is something I have been wanting to learn for a while but was unsure how to do it. I learned this technique from a video created by pur3h4t3. I link to his blog can be found at the bottom of this entry.
You may want to create a custom wordlist using a companies website. What the method I am demonstrating will do is take a website, synjunkie.blogspot.com in this example, and create a wordlist using all the words on that site. Hopefully these words may be relevant to my target.
I will cover how to use this list with a password cracker in a later blog entry.
Tools
All tools i use are on the backtrack3 CD.
Creating the Wordlist
1. First I create a directory that I am going to download a copy of the website into. After changing to that directory I quickly grab the site using wget.
wget - r http://www.site.com

2. After grabbing the site I use wyd.pl to extract all the words from the site into a single file.
wyd.pl -n -o /root/sj/wordlist.txt /root/sj/synjunkie.blogspot.com/

3. I then cat the file that I have created out, piping it through sort and uniq, to put it in order and remove any duplicate words.
cat wordlist.txt | sort | uniq > wordlist2.txt

This then gives me a file called wordlist2.txt that is a bit smaller as the duplicates have been removed.
4. Next I use pw-inspector to go through the file and remove any words that do not meet the criteria.
cat wordlist2.txt | pw-inspector -m 1 -M 20 >customlist.txt
The criteria I have set here is words should be a minimum of 1 letter and a maximum of 20. If you know that your target hes a minimum password legnth of 8 characters you could remove all words with less than 8 characters using this tool.

6. The result is a file called customlist.txt that contains words that may be more relevant to a target.
cat customlist.txt

Links
http://pur3h4t3.blogspot.com
http://www.remote-exploit.org/backtrack.html
NEVER HaCKEr
Vspan style="font-weight: bold; color: #ff0000;"Cydv l[hf:VLspanC Why Physical Access Wins



 المواضيع المتشابهه
المواضيع المتشابهه 




































 العرض العادي
العرض العادي



