السلام عليكم ورحمة الله وبركاته ntroduction
HijackThis is a utility that produces a listing of certain settings found in your computer. HijackThis wills scan your registry and various other files for entries that are similar to what a Spyware or Hijacker program would leave behind. Interpreting these results can be tricky as there are many legitimate programs that are installed in your operating system in a similar manner that Hijackers get installed. Therefore you must use extreme caution when having HijackThis fix any problems. I can not stress how important it is to follow the above warning.
There are two prevalent tutorials about HijackThis on the Internet currently, but neither of them explain what each of the sections actually mean in a way that a layman can understand. This tutorial, in addition, to showing how to use HijackThis, will also go into detail about each of the sections and what they actually mean. There is no reason why you should not understand what it is you are fixing when people examine your logs and tell you what to do.
If you would like to first read a tutorial on how to use Spybot, you can click here:
How to use Spybot - Search and Destroy Tutorial
With that said, lets move on to the tutorial on how to use it. If you want to see normal sizes of the screen shots you can click on them. Keep in mind, that a new window will open up when you do so, so if you have pop-up blockers it may stop the image window from opening.
How to use HijackThis
HijackThis can be downloaded as a standalone executable or as an installer. The standalone application allows you to save and run HijackThis.exe from any folder you wish, while the installer will install HijackThis in a specific location and create desktop shortcuts to that executable. When using the standalone version you should not run it from your Temporary Internet Files folder as your backup folder will not be saved after you close the program. In order to avoid the deletion of your backups, please save the executable to a specific folder before running it. We suggest that you use the HijackThis installer as that has become the standard way of using the program and provides a safe location for HijackThis backups.
The first step is to download HijackThis to your computer in a location that you know where to find it again. HijackThis can be downloaded from the following links depending on the executable you wish to use:
HijackThis Standalone Download Link HijackThis Installer Download Link
If you have downloaded the standalone application, then simply double-click on the HijackThis.exe file and then
click here to skip to the part where the program has started.
Otherwise, if you downloaded the installer, navigate to the location where it was saved and double-click on the
HJTInstall.exe file in order to start the installation of HijackThis. When the install starts, click on the
Install button to have HijackThis installed into the
C:\Program Files\Trend Micro\HijackThis folder, create a desktop shortcut that can be used to run the program when you need to, and to automatically launch HijackThis for the first time.
You should now see a screen similar to the figure below:

Figure 1. HijackThis Startup screen when run for the first time
We suggest you put a checkmark in the checkbox labeled Don't show this frame again when I start HijackThis, designated by the blue arrow above, as most instructions you will given will not account for this screen. After you have put a checkmark in that checkbox, click on the None of the above, just start the program button, designated by the red arrow in the figure above. You will then be presented with the main HijackThis screen as seen in Figure 2 below.

Figure 2. Starting Screen of Hijack This
You should first click on the Config button, which is designated by the blue arrow in Figure 2, and confirm that your settings match those found in Figure 3 below. The options that should be checked are designated by the red arrow.

Figure 3. HijackThis Configuration Options
When you are done setting these options, press the back key and continue with the rest of the tutorial.
To have HijackThis scan your computer for possible Hijackers, click on the Scan button designated by the red arrow in Figure 2. You will then be presented with a screen listing all the items found by the program as seen in Figure 4.

Figure 4. Scan Results
At this point, you will have a listing of all items found by HijackThis.
If what you see seems confusing and daunting to you, then click on the Save Log button, designated by the red arrow, and save the log to your computer somewhere you will remember later.
To open up the log and paste it into a forum, like
ours, you should following these steps:
- Click on Start then Run and type Notepad and press OK. Notepad will now be open on your computer.
- Click on File and Open, and navigate to the directory where you saved the Log file.
- When you see the file, double click on it. The log file should now be opened in your Notepad.
- Click on Edit and then Select All. All the text should now be selected.
- Click on Edit and then Copy, which will copy all the selected text into your clipboard.
- Go to the message forum and create a new message.
- Title the message: HijackThis Log: Please help Diagnose
- Right click in the message area where you would normally type your message, and click on the paste option. The previously selected text should now be in the message.
- Press Submit
If you would like to see information about any of the objects listed, you can click once on a listing, and then press the "
Info on selected item..." button. This will bring up a screen similar to Figure 5 below:

Figure 5. Object Information
When you are done looking at the information for the various listings, and you feel that you are knowledgeable enough to continue, look through the listings and select the items you would like to remove by placing checkmarks in the checkboxes next to each listing as shown in Figure 6. At the end of the ******** we have included some basic ways to interpret the information in these log files. By no means is this information extensive enough to cover all decisions, but should help you determine what is legitimate or not.

Figure 6. Select an item to Remove
Once you have selected the items you would like to remove, press the Fix Checked button, designated by the blue arrow, in Figure 6. HijackThis will then prompt you to confirm if you would like to remove those items. Press Yes or No depending on your choice.
for analyzing the log file go to
http://www.hijackthis.de/en
Dlk h[g hod DaRk DrEaM




 المواضيع المتشابهه
المواضيع المتشابهه 









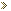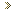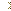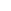




 العرض العادي
العرض العادي



